Have you encountered porn sites or some unwanted adverts popping out on your computer screen recently? The chances are you might have malware on your system; or as Ara Labs’ new discovery depicts a new malware on your router.
As if we don’t have much to worry about when browsing the internet, yet here we are again with a new router malware recently discovered. This malware is said to be designed injecting ads and pornography into websites.
As much as a lot of malware do this kind of annoyance, this so-called new router malware is a bit different, and by different I mean modifying your router’s DNS settings to intercept Google Analytics tags and then replacing them with malicious content. Router DNS hijacking is not a new thing and has already been around for a while now. As mentioned before, this malware uses the hijacking to target the Google Analytics tags.

Hijacking Google Analytics
Google Analytics is currently the most preferred traffic analytics service that provides the ability to track and analyze website traffic. This makes it the perfect target for the Black hat hackers. By already having a hijacked DNS through your router, the fraudsters will now intercept requests with Google Analytics and redirecting them to a fake site with malicious JavaScript that then injects the reported porn and unwanted ads when browsing.
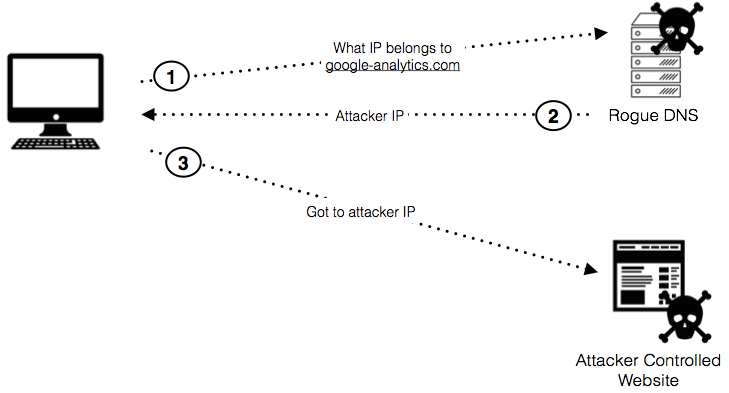
How Does This Hijacking Work?
Google’s DNS server is known to be 8.8.8.8, but with a hijacked DNS, the primary DNS is set at 91.194.254.105 which is a rogue DNS server and thus making your legitimate Google DNS as secondary. While the rouge DNS server will mostly refuse most domains, it will forcibly rely on the secondary DNS server which is 8.8.8.8. When checking the Google Analytics domain, it responds with a different IP, 195.238.181.169, which certainly is not a valid Google server. By using this fake server through browsing, you will then experience malicious JavaScript injecting ads into the website that is hosting the Google Analytics tag.
Removal And Prevention
Unfortunately I have experienced this malicious content popping out on my screen just recently, but with a few searches here and there, I was quite happy with the results. As the saying goes, ‘Where there’s a will, there is a way.’
Here are some steps which I found useful to help prevent DNS hijacking:
- Make sure your system is not affected by any malware. Scan your system for virus and malware with your security application. If you don’t have one, you should. You can simply download free malware removal tools.
- Clear browsing history, cookies, cache and uninstalling unwanted browser plug-ins.
- Try changing your DNS server.
- Make sure your firmware on your router is fully patched and change default credentials.
If you want to be more secure there are plenty of guides online for router DNS hijack prevention.